Setting up authorization
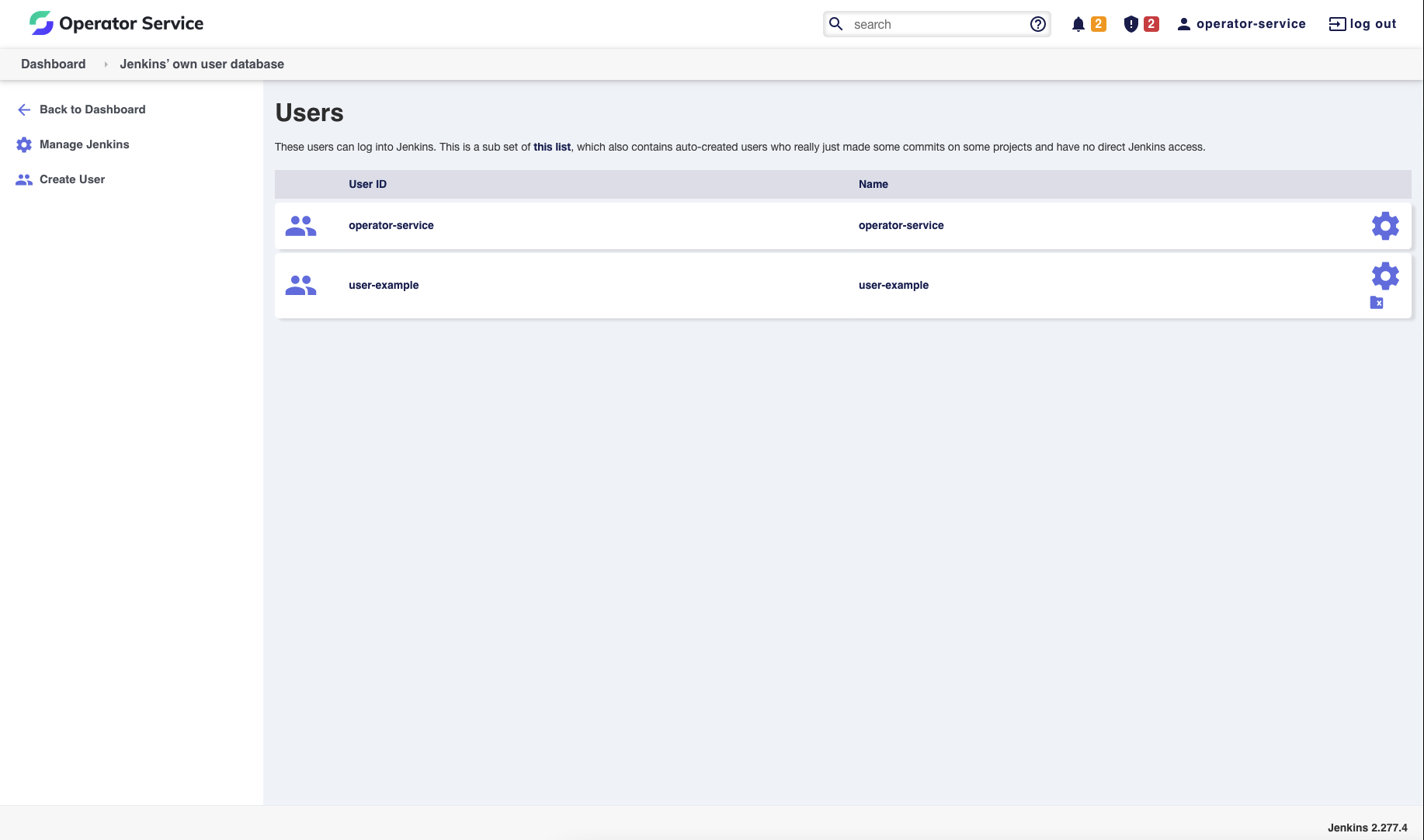
In order to assign permissions, first you will need to have a set of users available in Jenkins. We highly recommend using one of the
provided Authentication strategies.
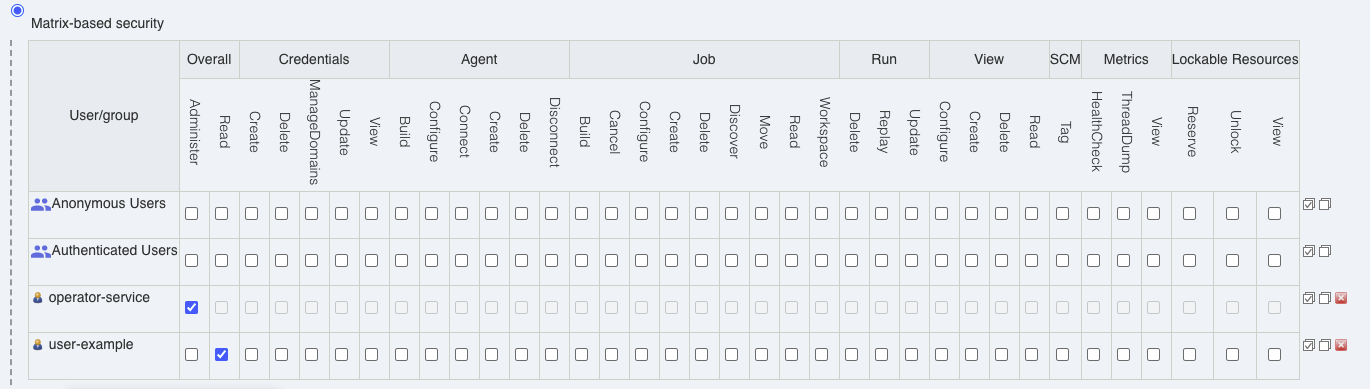
Before creating an authorization custom resource, you need to install matrix-plugin. The Operator Service will look for its declaration in the Jenkins Custom Resource.
Prepare a custom resource with matrix-based authorization. Provide a users with all wanted permissions.
operator-service username is not allowed and operator will block Custom Resource from applying.
apiVersion: operator-service.com/v1beta1
kind: JenkinsAuthorization
metadata:
name: matrix-example
namespace: default
labels:
operator-service.com/jenkins: example
spec:
type: matrix
matrix:
users:
- name: user-example
permissions:
- Overall/Read
Create it in the Kubernetes:
$ kubectl apply -f matrx-authz.yaml
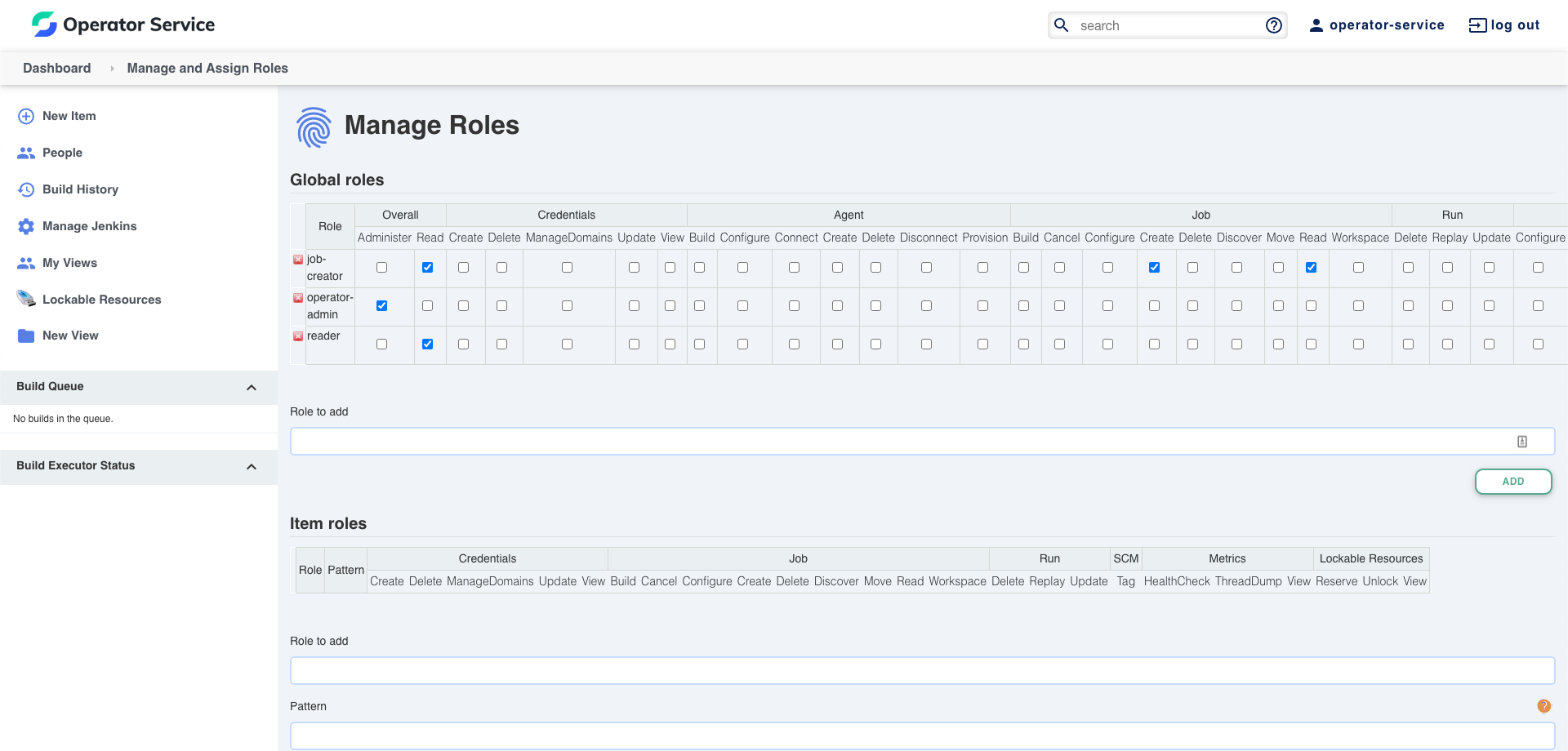
Next check if all permissions where successfully granted to all users. You can check it in “Configure Global Security” tab in Jenkins settings.
Define roles and assign users.
In order to use Role-based Authorization Strategy, you need to install role-strategy plugin. The Operator Service will look for its declaration in the Jenkins Custom Resource.
Below you can see an exemplary JenkinsAuthorization Custom Resource. You need to specify the type of authorization strategy and define the roles. Each role must have a unique name, corresponding permissions and users or groups, to which it will be assigned.
apiVersion: operator-service.com/v1beta1
kind: JenkinsAuthorization
metadata:
name: role-example
namespace: default
labels:
operator-service.com/jenkins: example
spec:
type: roleBased
roleBased:
roles:
- name: reader
permissions:
- Overall/Read
usersOrGroups:
- anonymous
- name: job-creator
permissions:
- Job/Create
- Job/Read
usersOrGroups:
- Martin
- Diana
Create it in the Kubernetes:
$ kubectl apply -f role-authorization.yaml
The newly created roles can be found in the UI: