Setting up authentication
Use your GitHub organisation to authenticate in Jenkins.
In order to use GitHub OAuth, you need to install github-oauth plugin. The Operator Service will look for its declaration in the Jenkins Custom Resource.
First register your Jenkins in your GitHub organisation according to GitHub docs.
- Homepage URL is the root to the Jenkins UI url (eg. http://localhost:8080)
- Authorization callback URL provide the root to the Jenkins UI url with trailing “/securityRealm/finishLogin” (eg. “http://localhost:8080/securityRealm/finishLogin”)
Copy the clientSecret for use in the Operator Service and the clientID. You will need them in the next steps.
Prepare a secret resource with the client secret acquired from GitHub in the Jenkins namespace. Connect the secret to the JenkinsAuthentication Custom Resource via label.
apiVersion: v1
kind: Secret
metadata:
namespace: <jenkins-namespace>
name: githubClientSecret
labels:
"operator-service.com/jenkinsauthentication" : "githubOAuth"
stringData:
clientSecret: <client-secret-from-GitHub>
Create it in the Kubernetes:
$ kubectl apply -f githubSecret.yaml
Next prepare the JenkinsAuthentication Custom Resource:
apiVersion: operator-service.com/v1beta1
kind: JenkinsAuthentication
metadata:
name: githubOAuth
namespace: <jenkins-namespace>
labels:
operator-service.com/jenkins: example
spec:
type: "githubOAuth"
githubOAuth:
clientSecretRef:
namespace: <jenkins-namespace>
name: githubClientSecret
clientID: <clientID-from-GitHub>
Create the JenkinsAuthentication Custom Resource in the Kubernetes:
$ kubectl apply -f jenkins-authentication.yaml
Additionally, you can specify different permission scopes. More information about different scopes can be found here. By default, the Operator Service sets these to “read:org” and “user:email”.
If you are using GitHub enterprise you can specify APIURI and WebURI. More information can be found in the GitHubOAuthAuthenticationConfig section of the schema
Use your Google organisation to authenticate in Jenkins.
In order to use GoogleHub OAuth, you need to install google-login plugin. The Operator Service will look for its declaration in the Jenkins Custom Resource.
Go to the GCP console.
If you do not have a project for Jenkins, you will need to create one. You will need to create an OAuth consent screen in the project. Next create credentials for Jenkins.
Click the “+CREATE CREDENTIALS” button and select OAuth client ID.
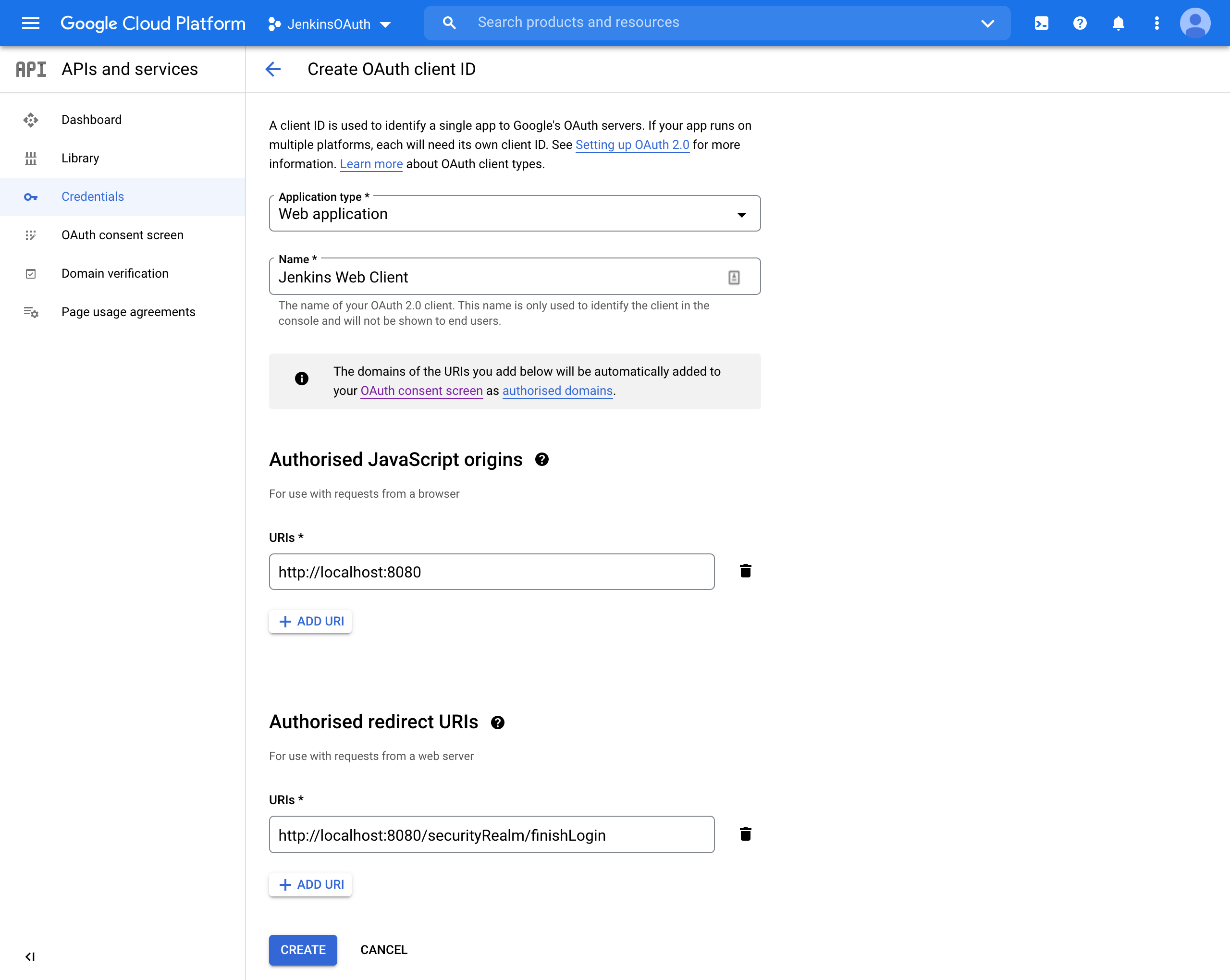
 You will need to provide the main Jenkins URI and the redirect URI. Redirect URI is the URI with trailing “/securityRealm/finishLogin”.
You will need to provide the main Jenkins URI and the redirect URI. Redirect URI is the URI with trailing “/securityRealm/finishLogin”.
 Click “CREATE” and copy the Client Secret and the Client ID from the pop up window. You will need them in the next steps.
Click “CREATE” and copy the Client Secret and the Client ID from the pop up window. You will need them in the next steps.
Prepare a secret resource with the client secret acquired from GitHub in the Jenkins namespace. Connect the secret to the JenkinsAuthentication Custom Resource via label.
apiVersion: v1
kind: Secret
metadata:
namespace: <jenkins-namespace>
name: googleClientSecret
labels:
"operator-service.com/jenkinsauthentication" : "googleOAuth"
stringData:
clientSecret: <client-secret-from-GCP>
Create it in the Kubernetes:
$ kubectl apply -f googleSecret.yaml
Next, prepare the JenkinsAuthentication Custom Resource:
apiVersion: operator-service.com/v1beta1
kind: JenkinsAuthentication
metadata:
name: googleOAuth
namespace: <jenkins-namespace>
labels:
operator-service.com/jenkins: example
spec:
type: "googleOAuth"
googleOAuth:
clientSecretRef:
namespace: <jenkins-namespace>
name: googleClientSecret
clientID: <clientID-from-GCP>
domain: ""
Note: If you are using localhost you do not have to provide the domain field at all. Use this field if you have a public domain for your Jenkins.
Create the JenkinsAuthentication Custom Resource in the Kubernetes:
$ kubectl apply -f jenkins-authentication.yaml
More information can be found in the GoogleOAuthAuthenticationConfig section of the schema
Use various identity providers compliant with OpenID Connect standard.
In order to use OpenID Connect Auth, you need to install oic-auth plugin. To do that, you can refer to (configuring plugins section) of Customizing Jenkins documentation page.
Prepare a secret resource with the client secret acquired from your identity provider in the Jenkins namespace. Connect the secret to the JenkinsAuthentication Custom Resource via label.
apiVersion: v1
kind: Secret
metadata:
namespace: <jenkins-namespace>
name: openIDConnectSecret
labels:
"operator-service.com/jenkinsauthentication" : "openIDConnectAuth"
stringData:
clientSecret: <client-secret-from-identity-provider>
Create it in the Kubernetes:
$ kubectl apply -f openIDSecret.yaml
Next, prepare the JenkinsAuthentication Custom Resource, specifying either auto or manual configuration.
Below you can find the minimal set of configured variables required to work with OpenID Connect Authentication with automatic configuration. Note that with this mode of configuration, you have to specify the well-known OpenID configuration URL.
apiVersion: operator-service.com/v1beta1
kind: JenkinsAuthentication
metadata:
name: openIDConnectAuth
namespace: <jenkins-namespace>
labels:
operator-service.com/jenkins: example
spec:
type: "openIDConnectAuth"
openIDConnectAuth:
clientID: <client-id-from-identity-provider>
clientSecretRef:
namespace: <jenkins-namespace>
name: openIDConnectSecret
autoManualConfigure: auto
wellKnownOpenIDConfigurationURL: <well-known-configuration-url-from-identity-provider>
Alternatively, you can use manual configuration mode. In this case, you need to specify at minimum the URL of the token server and URL of the authorization server. Below you can find sample yaml with minimal configuration.
apiVersion: operator-service.com/v1beta1
kind: JenkinsAuthentication
metadata:
name: openIDConnectAuth
namespace: <jenkins-namespace>
labels:
operator-service.com/jenkins: example
spec:
type: "openIDConnectAuth"
openIDConnectAuth:
clientID: <client-id-from-identity-provider>
clientSecretRef:
namespace: <jenkins-namespace>
name: openIDConnectSecret
autoManualConfigure: manual
tokenServerURL: <token-server-url-from-identity-provider>
authorizationServerURL: <authorization-server-url-from-identity-provider>
